ZIVAME DATA BREACH EXPLODES! NCW summons Zivame Founder; hacker group who leaked database exposes its security researcher’s "Unauthorised Activity"
Total Views | 360
In yet another development in the Zivame Databreach incident, the National Commission for Women (NCW) has taken Suo Moto Cognizance of Twitter post by legal activism group, Kalinga Rights Forum on Wednesday & has issued notice to Ms. Richa Kar, Founder of Zivame Retail, Apparel & Fashion in the matter of Leaking of sensitive information of 1.5 Million Hindu girls to Islamic groups through Darkweb for targeted harassments, Lovejihad, women trafficking & abduction.
NCW in its notice dated 24th May 2023 has called Richa Kar, Founder of Zivame for a hearing at its office at 12pm Noon. She has to appear before the commission in Person. The notice’s copy is also issued to Ms Amisha Jain , CEO of Zivame Retail, Apparel & Fashion as well as Ms Lavanya Pachisia, CEO of Zivame.

The news is broken by Legal activism group Kalinga Rights Forum in its latest Twitter post
ALLEGED HACKER GROUP “SHADOW HACKER” EXPOSES ZIVAME’s SECURITY RESEARCHER Monish Kaul “Unauthorised Actions” that led to the DATA BREACH of 1.5 Million Hindu girls in ZIVAME
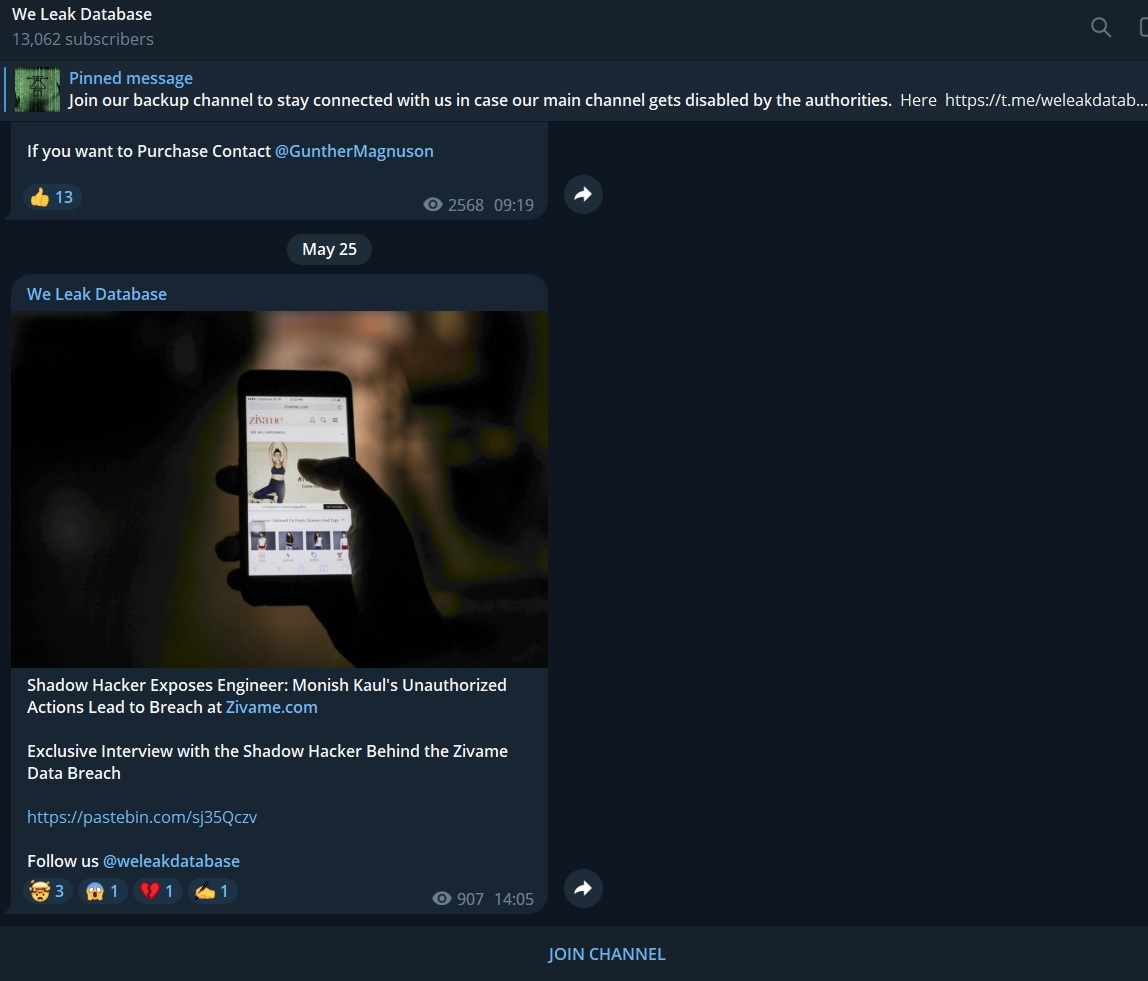
The hacker group Shadow Hacker has now accused Monish Kaul’s for his “Unauthorised actions” that led to the breach of data of 1.5 million Hindu girls in a post which is shared by “We Leak Database” the same telegram channel which was selling database of 1.5 million Hindu girls for 400USD.
The Hacker group SHADOW HACKER in a Post wrote :
“Hello, I am here to expose Monish Kaul, the engineer of http://Zivame.com. Let me tell you the story. First, I found a vulnerability on http://Zivame.com and reported it via email to ********@zivame.com. You can check if you work there. I also asked them for a bounty. Monish contacted me on Telegram since I had provided him with my Telegram handle, and we started to negotiate. During our conversation, he informed me that he was dealing with me illegally and unofficially, without the knowledge of his superiors and the company. This lack of official involvement is the main reason behind the breach. We agreed on a deal for $1500. I closed the bug with him, fixed everything, and everything seemed fine. I want to emphasize that I never sold any data or attempted to cause further damage. However, after a few days, I contacted him again and informed him that I had discovered a new vulnerability that allowed me to take over any Hindu girl's account on the platform! To my surprise, he ignored me and told me that he was not interested, stating that since he had already paid me before, I should have provided the information for free. However, I had only asked for $500. I have provided evidence in the form of pictures, which can be found at this link: https://imgur.com/a/5IG0f6t . Despite my concerns, he acted indifferent and expressed no interest. This made me furious, leading me to expose http://Zivame.com. I can confidently state that he is the main reason behind the breach, as I am the individual who breached Zivame. I hold Monish Kaul responsible for this incident. Once again, I want to mention that Zivame can verify the logs of the webmail, the messages sent, and confirm that we had a conversation with him, establishing his involvement without the company's approval. TechCrunch informed India’s computer emergency response team CERT-In about the availability of data samples on Friday.
“We are already in process of taking appropriate action with the concerned authority,” CERT-In said in reply. Zivame declined to comment on the apparent breach when reached by TechCrunch. When reached via LinkedIn, Zivame chief technology and product officer Monish Kaul opened and read our message, but did not respond.”
Telegram channel “WE LEAK DATABASE” Still Selling 1.5 Million Hindu girls data of Zivame at 300USD
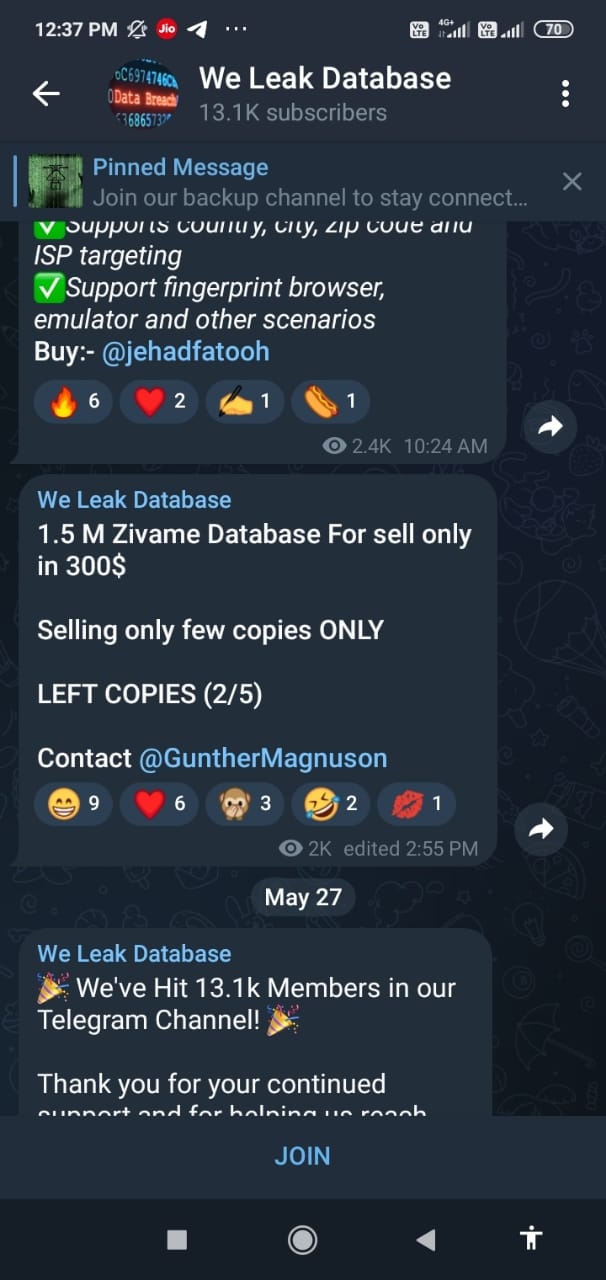
Earlier a Twitter user & Journalist (@Cyber_Huntss) exposed this data breach leading to the Legal Activism group Kalinga Rights Forum filing Complaints to the Ministry of Home Affairs, the Ministry of Electronics & Information Technology as well as WCD Ministry.
Currently Status of the complaints with the above government ministries are said to be “UnderProcess”.
Bharati Web







